
Download Jt WhatsApp App Updated

Screenshot Gallery
Jt WhatsApp Overview
JTWhatsApp Overview: A Modified Client with Extended Controls for Android Messaging
JTWhatsApp positions itself as a modified (MOD) edition of the official WhatsApp application; the mod expands privacy, customization, and media capabilities beyond the standard client. The project attributes development to JiMODs (Jimtechs Edition); the distribution presents itself as an “anti-ban APK” intended to operate alongside or in place of the official build. The report frames JTWhatsApp as a case study in user demand for granular control; the analysis situates the app within a wider landscape of unofficial clients that trade platform compliance for feature breadth.Developer and Ecosystem Placement
JiMODs (Jimtechs Edition) serves as the developer; the developer claims encryption hardening and account protection. The material does not specify a publisher, release date, engine, or formal game modes; the text instead emphasizes the mod’s privacy toggles, interface theming, and transport limits. The ecosystem relation places JTWhatsApp in the family of third-party APKs; the mod relies on Android’s sideloading pathway rather than an official store channel.Platform and Distribution Posture
The application targets Android; the report describes installation via an APK file obtained outside the Google Play Store. The source does not document iOS availability; the documentation restricts its procedural guidance to Android devices. The mod labels itself “anti-ban”; the text asserts that newer versions strengthen defenses while also acknowledging the possibility of temporary bans.Core Feature Analysis: Privacy, Anti-Overrides, Theming, and Throughput
Enhanced Privacy and Anonymity Controls
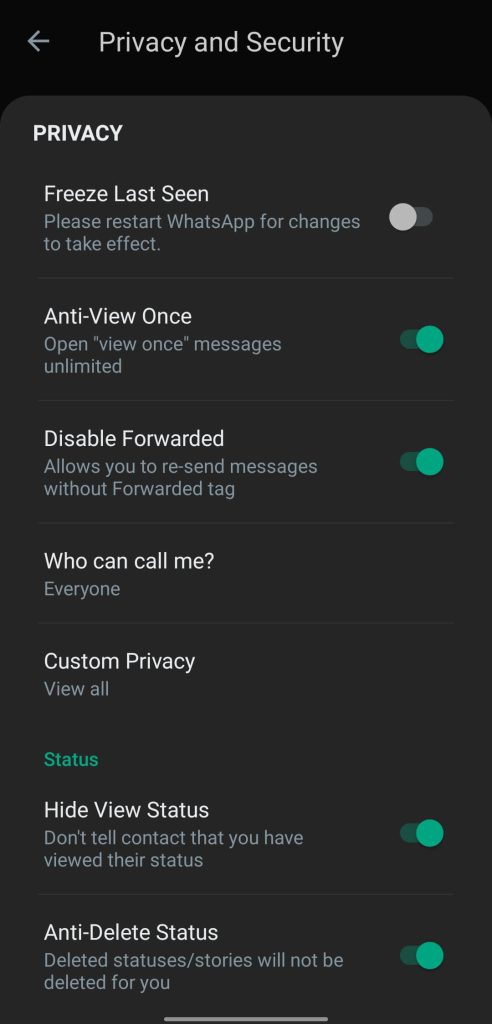
The mod grants per-signal masking and read-state deferral; the controls aim to let users curate visibility across presence, reading, and interaction cues.- Freeze Last Seen: The feature hides online presence; contacts cannot observe active use.
- Who Can Call Me: The setting restricts inbound voice and video calls; the user whitelists permitted callers.
- Hide View Status: The toggle enables covert status viewing; the user’s name does not appear in viewer lists.
- Read Receipt Management: The options span “Hide Blue Ticks,” “Hide Second Tick,” and “Show Blue Ticks After Reply”; the logic defers or suppresses delivery and read signals.
- Activity Obfuscation: The controls hide “typing” and “recording” indicators; interlocutors cannot detect message composition or voice-note preparation.
- Hide Blue Microphone: The state conceals voice-note consumption; the sender cannot confirm playback.
- Disable Forwarded: The mod removes the “Forwarded” attribution; forwarded messages appear as original posts from the user.
Anti-Features That Override Standard Constraints
The “Anti-” suite targets ephemeral media locks, recall controls, and account safety; the functions intentionally bypass official limitations.- Anti-View Once: The feature nullifies single-view media; photos and videos marked “View Once” remain accessible for multiple views.
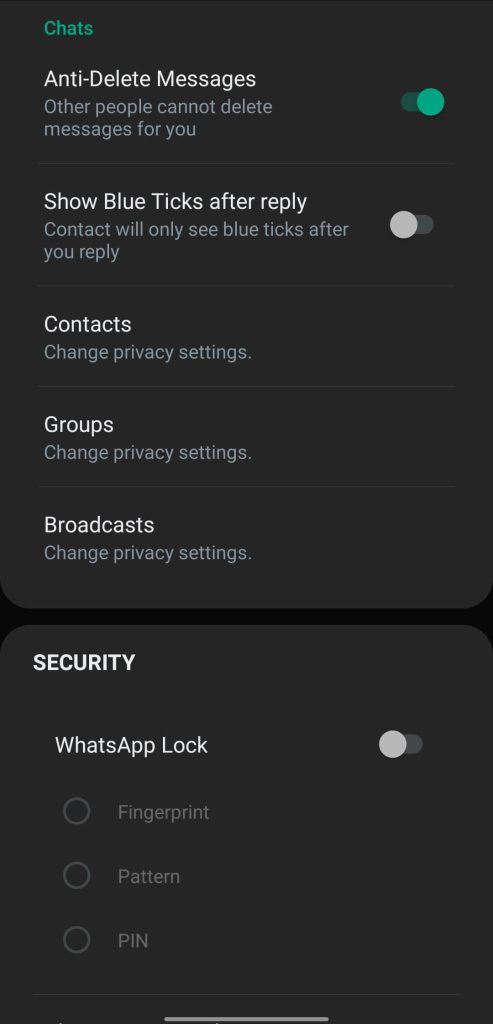
- Anti-Delete Status: The logic preserves status updates; deleted statuses remain visible to the JTWhatsApp user.
- Anti-Delete Messages: The override blocks message revocation; messages deleted “for everyone” persist on the recipient’s device.
- Anti-Ban Protection: The package asserts account-protection measures; the documentation associates the latest versions with improved safeguards.
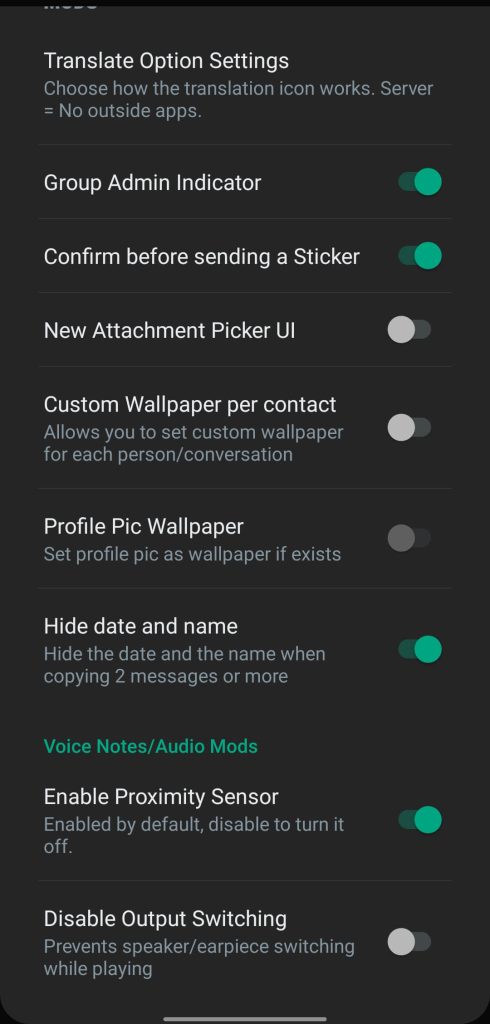
Unparalleled Customization and Theming
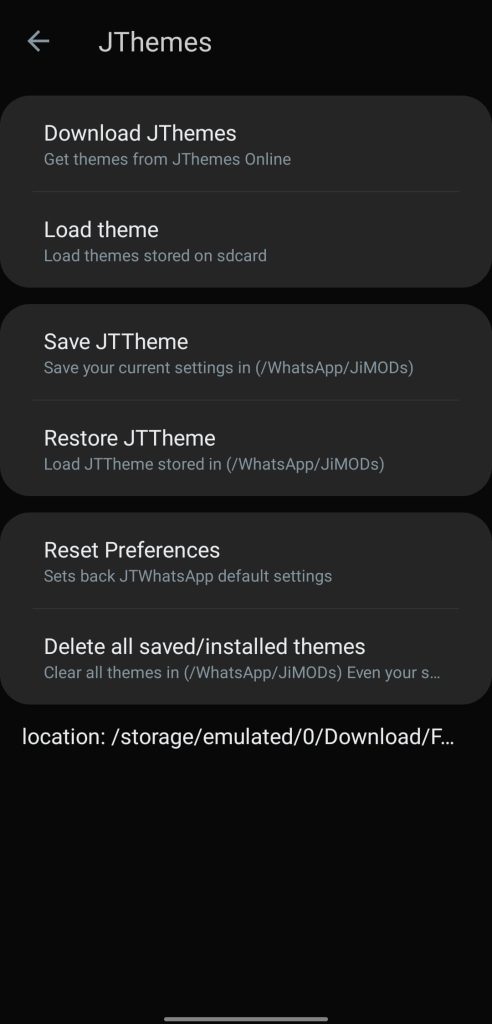
The theming subsystem extends beyond wallpaper swaps; the system exposes global palettes, iconography, font choices, and screen-specific motifs.- Theme Library and State: The “JTThemes” catalog lists more than 4000 themes; local load/save operations enable portable configurations.
- Universal Styling: Users modify Action Bar, Background, Status Bar, and Navigation Bar; emoji packs, font styles, launcher icons, and notification icons vary by preference.
- Home-Screen Controls: Header, row layout, floating action button, and status screen receive bespoke styles; a “Viewed Story Toast” and “Hide Chats Divider” option refine feedback and density.
- Chat-Screen Controls: Action Bar, bubble/tick visuals, profile-photo presentation, and entry-field style accept overrides; per-contact wallpapers and “Confirm before sending a Sticker” mitigate accidental sends.
- Widget Styling: The home-screen widget exposes background and text-color parameters; contact names and statuses adopt customized contrast.
Expanded Media and Messaging Capacities
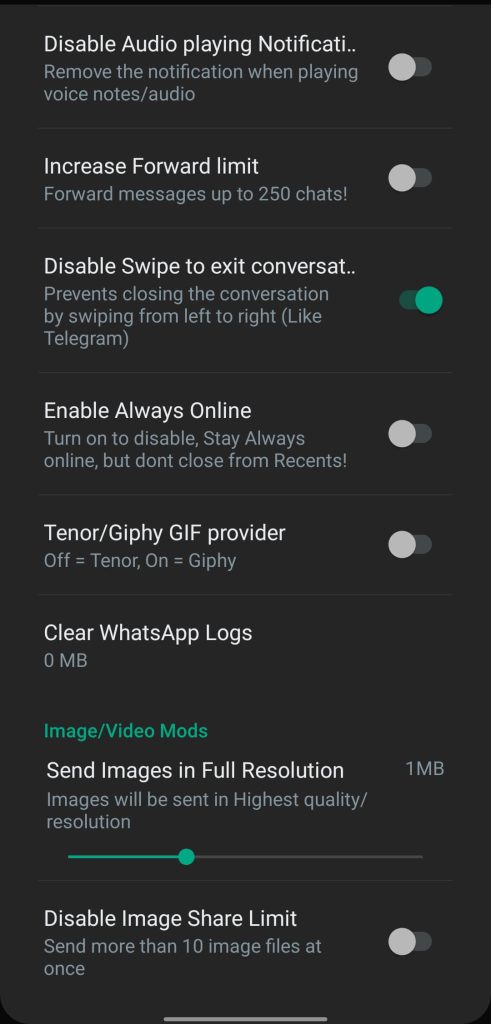
The mod raises ceilings across status duration, broadcast size, forwarding fan-out, and binary payload size; the changes directly affect community coordination and media workflows.- Maximum Video Status Duration: Official limit sets 30 seconds; JTWhatsApp extends to 5 minutes.
- Status Text Length: Official limit caps at 50 characters; JTWhatsApp extends to 255 characters.
- Broadcasting Messages: Official ceiling targets 256 contacts; JTWhatsApp scales to 1024 contacts.
- Forwarding Capacity: Official limit allows 10 recipients; JTWhatsApp permits 250 recipients.
- Image Batch Sharing: Official client moves 30 images per send; JTWhatsApp raises the batch to 90 images.
- Video and Audio File Size: Official limit restricts to 16 MB; JTWhatsApp raises the cap to 1 GB.
Safety, Security, and Risk Appraisal
The security posture combines local locking with contested safety claims; the posture remains mixed because unofficial distribution introduces systemic risk. The app exposes a built-in lock (PIN, password, or fingerprint); the interface offers an invisible-pattern option and vibration suppression to reduce side-channel cues. The developer describes the build as “absolutely safe” and “official anti-ban”; the text states that the code is encrypted for user protection. The same material warns that the mod “may not be as secure as the official WhatsApp client” and is “most prone to getting hacked easily”; the guidance advises users to download at their own risk. The report concedes a “risk of temporary ban”; the recommended mitigation instructs users to update to the latest version that allegedly strengthens anti-ban routines.Installation and Data Migration for Android
APK Installation Procedure
The installation path utilizes Android’s sideloading capability; the process differs from a store-based workflow.- Open system settings and navigate to security controls; enable “Unknown Sources” to authorize third-party APK installation.
- Acquire the JTWhatsApp APK file; the report cautions that source trust is hard to validate and that malware risk exists.
- Open a file manager and locate the downloaded package; tap the file to initiate the installer and accept the prompts.
- Launch the application and agree to terms; enter the phone number and complete standard verification.
Recommended Chat-Migration Path: Automated Data Copy
The report documents a guided migration step in certain builds; the utility attempts a one-click copy from the official client.- Open the official WhatsApp and create a fresh local backup via Settings > Chats > Backup.
- Install the JTWhatsApp APK.
- Launch JTWhatsApp and locate the Copy WhatsApp Chat Data button on the initial screen; run the copy before number verification.
- Wait for confirmation that the data copy completes; proceed with number verification to trigger local-restore detection.
Alternative Chat-Migration Paths: Manual Folder Operations
The manual avenues rely on Android’s scoped storage directories; the exact paths vary by version, and success is not guaranteed. Procedure A: Folder Renaming- Generate a local backup in the official client via Settings > Chats > Backup.
- Open a file manager and navigate to Android/media/.
- Find com.whatsapp and rename the directory to com.jtwhatsapp.
- Inside the renamed directory, locate the WhatsApp subfolder and rename it to JTWhatsApp; the final path becomes /Android/media/com.jtwhatsapp/JTWhatsApp/.
- Install and launch JTWhatsApp; verify the number and allow the app to discover and restore the backup.
- Create a local backup in the official client.
- Navigate to Android > media > com.whatsapp and copy all contents.
- Paste the data into the JTWhatsApp target folder, which the material exemplifies as Jtwhatsapp > JiMODs > com.whatsAppJT.
- Run any in-app restore control if required; the documentation references a path such as JiMODs > Backup and Restore > Restore Whatsapp data.
Semantic Mapping to Game-Like Metadata for Catalog Consistency
Catalog taxonomies on APK download sites often mirror game schemas; the report enables partial mapping while acknowledging absent fields. The developer maps to JiMODs (Jimtechs Edition); the publisher is not specified in the source. The release date is not provided; the documentation does not enumerate a version timeline. The genre maps most closely to “communication client—modified WhatsApp variant”; the engine is not discussed. The platform maps to Android via sideloaded APK; iOS is not documented. The game modes field does not apply; the report prioritizes messaging feature mechanics such as read-receipt control, call gating, status viewing privacy, and media-limit expansion.Feature Mechanics Summary for Catalog Snippets
- Presence Control: The app freezes last-seen, hides typing/recording, and defers read receipts until reply.
- Status/View Overrides: The build hides view attribution and defeats “View Once” limits.
- Recall Resistance: The client displays deleted messages and deleted statuses to the recipient.
- Call Firewall: The user restricts inbound calls to selected contacts.
- Theming System: The library exceeds 4000 themes; the interface accepts granular per-screen styling.
- Media Throughput: The payload limit rises to 1 GB; batch sizes and status durations scale substantially.
- Local App Lock: The app enforces PIN/password/fingerprint access with stealth pattern options.
Risk–Benefit Balance for Prospective Users
The feature delta favors power users; the controls materially change how presence, delivery, and media behave across contacts. The risk ledger documents nontrivial exposure: the distribution channel bypasses store vetting, the client may face temporary account bans, and the security assurances coexist with explicit warnings in the same promotional corpus. The guidance therefore situates JTWhatsApp as a utility for users who consciously accept unofficial-app trade-offs; the decision calculus weighs functional autonomy against ecosystem support and platform policy.Conclusion
JTWhatsApp, as characterized by the report, extends WhatsApp’s baseline with privacy toggles, anti-restriction overrides, a deep theming stack, and lifted transport ceilings; the package appeals to users seeking fine-grained control over how their messaging signals are exposed and how their media flows. The Android-only sideloading model introduces risk; the same documentation that asserts anti-ban and encryption benefits also cautions about hackability and potential bans. The adoption decision ultimately aligns with user priorities: the subject values customization and capability, the relation connects those values to a third-party client, and the object registers the practical and security consequences of operating outside the official ecosystem.JT WhatsApp Gameplay Guide: Systems, Strategies, and Mastery Pathways
JT WhatsApp positions a player within a feature-dense communication environment that operates like a sandbox of privacy mechanics, interface customization, and expanded messaging limits. The player engages the application as a toolkit where each control toggles visibility, reach, and tempo of interaction. The experience unfolds as the player configures rules that govern how contacts perceive presence, how messages persist, and how media circulates across chats and status feeds. This guide organizes those systems into actionable loops so the player can execute deliberate strategies while acknowledging inherent risks documented for this modified client.
Core Loop: Visibility Management as Moment-to-Moment Play
The player uses privacy switches to regulate informational flow between their account and their contacts. The Freeze Last Seen control sets the player–status–visibility relation by masking online presence, which changes how counterparts time their outreach. The Hide Typing and Hide Recording indicators set the player–activity–obfuscation relation by severing the usual feedback loop that reveals composition moments. The Hide Blue Ticks and Hide Second Tick toggles set the sender–receipt–confirmation relation by delaying or removing delivery and read confirmations. The Show Blue Ticks After Reply option sets the response–acknowledgment–release relation by coupling read status to a deliberate reply event. These mechanics collectively let the player pace exchanges like turns in a strategy title where initiative and tempo create advantage.
Call Firewall: Targeted Access as Defensive Play
The player applies the Who can call me setting to construct a whitelist that filters voice and video attempts. This setting defines the contact–permission–connection relation by granting or denying call initiation at a per-contact granularity. The mechanic functions as a defensive stat, since restricted access reduces interruptions and preserves focus windows for other tasks. The player thereby uses permission curation as a shield that moderates real-time engagements similar to cooldown management in competitive play.
Status Intelligence: Covert Observation and Reaction Windows
The player activates Hide View Status to watch contact updates without attribution. This feature defines the player–status feed–invisibility relation by removing view records from the poster’s list. The player then evaluates social signals without triggering counter-moves from observed contacts. The mechanic enables reconnaissance that informs subsequent messaging or silence, thereby reinforcing a low-profile approach to information gathering.
Persistence Control: Anti-Delete and Anti-View Once as Resource Retention
The player exploits Anti-Delete Messages and Anti-Delete Status to preserve content that other parties attempt to revoke. These toggles establish the sender–erasure–resilience relation by converting transient items into retained resources for the player. The Anti-View Once control extends consumption windows for single-use media, setting the media–restriction–bypass relation in favor of repeated access. These mechanics transform ephemera into archives, which support review, evidence keeping, and pacing that favors careful analysis over impulsive reactions.
Messaging Throughput: Capacity Expansion as Macro Advantage
The player leverages elevated ceilings to scale outreach and sharing. The extended limits set the player–distribution–bandwidth relation by raising forward counts, broadcast counts, image batch sizes, and permissible media file sizes up to substantially higher thresholds than the official baseline. The longer status duration sets the player–storytelling–runtime relation by enabling extended narrative segments. These allowances create macro advantage for community management, content seeding, and campaign-style dissemination that benefits power users and group organizers.
Customization Layer: Theming and Interface Tuning as UX Optimization
The player navigates a theme library with thousands of variants to align readability and aesthetics with task requirements. The themes system sets the player–interface–fit relation by swapping typography, emoji variants, iconography, and color schemes. Screen-specific controls further set the component–style–state relation by letting the player tune headers, rows, floating action buttons, chat bubbles, ticks, profile photo displays, and conversation entry styles. The widget customization sets the dashboard–glanceability–contrast relation by allowing background and text color adjustments for quick status checks. This layer upgrades ergonomics and reduces cognitive load across extended sessions.
Forwarding Identity: Provenance Control as Narrative Authority
The player activates Disable Forwarded to remove the “forwarded” attribution tag from shared items. This function sets the content–origin–presentation relation by decoupling visible provenance from the act of redistribution. The mechanic changes how recipients interpret authenticity and authorship, which can affect persuasion, trust, and conversational framing. The player should handle this capability with care, since altered provenance shifts expectations in social exchanges.
Security Posture: Protective Shells and Documented Risks
The player deploys the built-in lock feature with PIN, password, or fingerprint to secure local access. The lock function sets the device–app–gatekeeping relation by adding friction against unauthorized use. The developers claim code encryption and anti-ban protections, which set the app–platform–resilience relation as aspirational safeguards. The documentation simultaneously notes that the client may be less secure than the official application, that it is prone to compromise, and that a temporary ban risk exists. The player must therefore set the feature–benefit–risk trade-off consciously, since the meta-game includes nontrivial platform enforcement and security uncertainty.
Actionable Playbook: Tactics for Different Communication Scenarios
Tempo Control for High-Signal Conversations
The player enables Freeze Last Seen and Hide Typing for negotiations or sensitive discussions. These toggles set the participant–timing–opacity relation by preventing opponents from inferring pressure points during drafting. The player uses Show Blue Ticks After Reply to ensure that acknowledgment only accompanies a substantive response, which sets the reply–confirmation–coupling relation and reduces forced follow-ups.
Inbox Defense for Focus Blocks
The player configures Who can call me to admit calls from priority stakeholders while excluding general contacts. This configuration sets the focus–disruption–barrier relation by minimizing unexpected rings during deep work. The player pairs this with muted badges and stealth read receipts to maintain silent monitoring without engagement, which preserves situational awareness while avoiding context switching.
Evidence Retention for Accountability
The player utilizes Anti-Delete Messages to maintain a record of agreements and changes. This option sets the message–revocation–immunity relation by keeping a stable audit trail after deletion attempts. The player complements this with Anti-View Once to re-examine visual materials for details, which sets the inspection–iteration–support relation and improves decision quality.
Broadcast Scaling for Community Managers
The player applies higher broadcast and forward limits to distribute updates across larger contact graphs. This move sets the campaign–reach–elasticity relation by expanding audience size without fragmenting messages. The player batches more images per send and uses longer status segments to stage cohesive narratives, which sets the content–coherence–throughline relation for event coverage or product showcases.
Tips and Best Practices
- The player pairs Hide Second Tick with Show Blue Ticks After Reply to control information leakage while preserving clear confirmation semantics on final response.
- The player assigns Custom Wallpaper per contact to set the chat–context–cue relation that reduces mis-sends in parallel conversations.
- The player activates “Confirm before sending a Sticker” to set the action–verification–safety relation that prevents accidental reactions in formal threads.
- The player uses widget text and background tuning to set the glance–legibility–contrast relation for outdoor or low-light scenarios.
- The player curates themes for high-density reading by selecting fonts and emoji sets that set the symbol–clarity–comfort relation over long sessions.
- The player exercises restraint with Disable Forwarded to set the ethics–provenance–integrity relation that maintains trust with discerning recipients.
- The player balances Anti-Delete features with discretion to set the privacy–consent–respect relation in sensitive exchanges.
Risk-Aware Strategy: Playing the Long Game
Operational Hygiene and Expectation Setting
The player communicates norms to close collaborators regarding delayed read receipts and invisible status views. This practice sets the team–protocol–alignment relation by reducing misinterpretations of silence. The player also treats retained messages as sensitive archives and limits redistribution, which sets the retention–stewardship–duty relation and avoids escalation in contentious threads.
Trade-Off Calculus for Feature Adoption
The player evaluates each capability against the documented risk landscape that includes security concerns and potential temporary bans. This evaluation sets the feature–exposure–threshold relation by enabling or disabling toggles based on scenario value rather than habit. The player periodically reviews configuration choices to ensure that aggressive visibility controls do not erode trust or collaboration outcomes.
Interface Mastery: Building a Personal Operations Theater
Screen-Specific Optimization
The player customizes the home screen rows, headers, and dividers to set the scan–priority–flow relation that surfaces critical chats. The player tunes chat bubbles and tick styles to set the recognition–parsing–speed relation that accelerates comprehension. The player adjusts action bar elements and profile photo displays to set the context–identity–recall relation that reduces cognitive overhead when juggling multiple conversations.
Notification Semantics
The player selects launcher and notification icons that set the alert–meaning–mapping relation for quick triage. The player configures toast behavior, such as “Viewed Story Toast,” to set the event–signal–awareness relation without entering threads. These choices create an ambient awareness layer that keeps the player informed while preserving the stealth profile established by privacy toggles.
Conclusion: Systems Literacy over Impulse
JT WhatsApp challenges the player to treat messaging as a systems game where privacy states, throughput limits, and interface ergonomics determine initiative and outcomes. The player who masters visibility mechanics sets interaction tempo with precision. The player who exploits persistence controls retains informational resources for later leverage. The player who scales distribution capitalizes on expanded ceilings to coordinate communities. The documented risks require sober judgment, so the winning strategy emphasizes configuration literacy, ethical use, and periodic recalibration. By aligning mechanics with intent, the player constructs an operations model that maximizes control while acknowledging the trade-offs inherent in a modified client.
